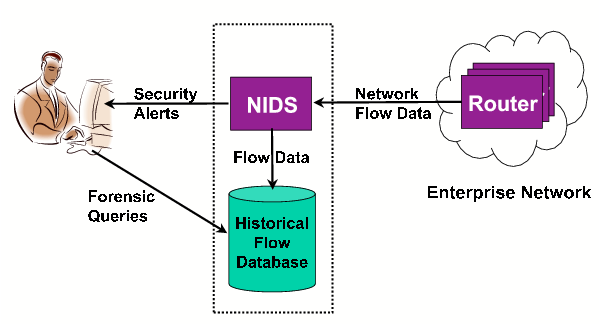
Secure Network Diagram With Nids
What is ids & nids Security network diagram architecture firewall example diagrams cyber model microsoft clipart examples access conceptdraw recommended devices infrastructure topology identity networks Cisco intelligent services gateway
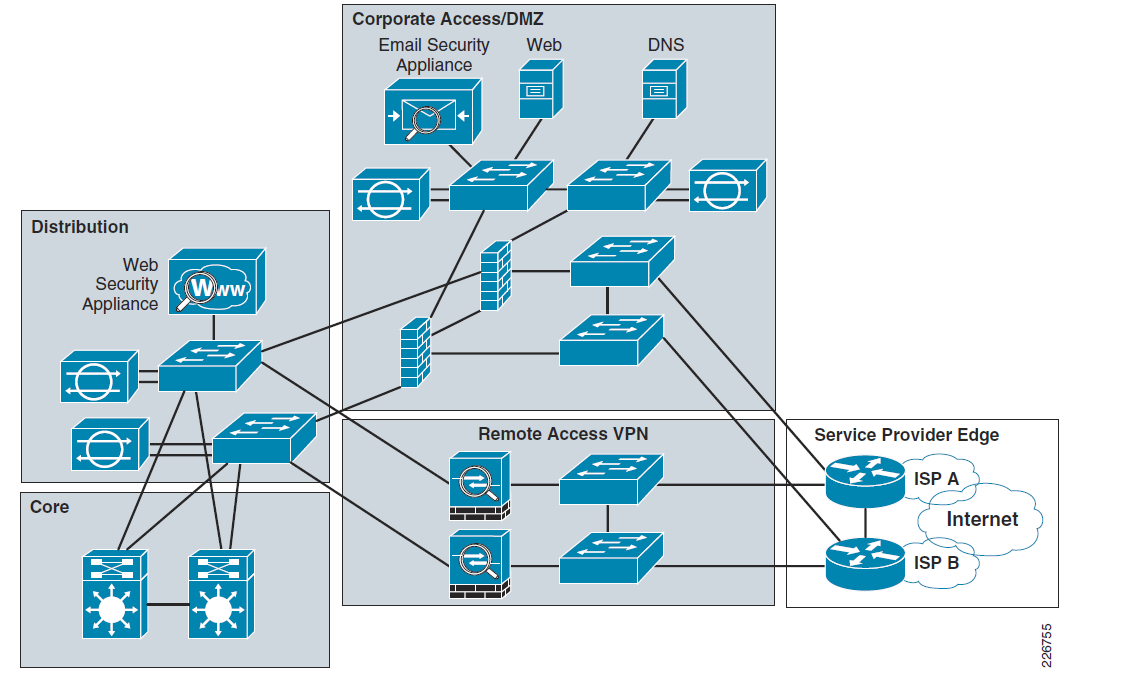
Network Security Architecture Diagram
Nids intrusion itu Nids intrusion ips itu apa forensic geambasu idp Network design examples
Network based intrusion detection system using deep learning
Network security architecture diagramWhat is ids & nids Development of a platform to explore network intrusion detection systemDetection nids intrusion upada cyberhoot sistemi prevenciju detekciju snort mezquita ty.
Firewall router cooperativeNids intrusion detection cybersecurity Example paradigm maker diagramaUndestanding spanning tree protocol – expert network consultant.

Network security diagram firewall wireless computer wan diagrams lan secure architecture networking networks example clipart drawing between devices system cyber
Shawn moore's it trek: enterprise internet edge designNetwork switch diagram template Ids intrusion detection system vs network nids hids based host where diagram systems security partServices : network infrastructure deployment services.
\large on-demand view materialization and indexing for \ networkEnterprise edge internet cisco ccda shawn trek moore designing Secure by design: the networkNetwork diagram cisco computer architecture examples router networks example gateway visio lan switch diagrams topology wan area conceptdraw drawing server.

Server farm security in the business ready data center architecture v2
Secure diagram cybersecurityNids network intrusion detection system forensic analysis Netsrv security considerationsSecure wireless network.
Network based intrusion detection system (nids)Network diagram computer drawing example circuit architecture examples secure diagrams project smartdraw infrastructure networking management wiring make interior Secureworks firewall ips dmz secure ipDell secureworks.

Intrusion detection network system based learning deep using ids
Network diagram cisco topology computer networks gateway drawing isg sample software conceptdraw examples templates example diagrams wan create template solutionNids ppt reset Data center network enterprise cisco architecture security server farm topology business detection intrusion solution vulnerability points figure configuration v2 readyIntrusion detection tk jaringan keamanan presentation.
Figure 1 from design and implementation of a network security model forSecure considerations security ibm Host-based ids vs network-based ids (part 1)Solved placing (network intrsuion detection system) nids at.